
MSDT: CVE-2022-30190 Vulnerability
C. BinKadal
---
Sendirian, Berhad
MSDT: CVE-2022-30190 Vulnerability (Follina)
QUICK AND DIRTY PATCH
A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word (From MicroSoft’s web, TL;DR).
This is a quick and dirty patch of MSDT: CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability (Follina). Assuming keeping your backup files in C:\tmp.
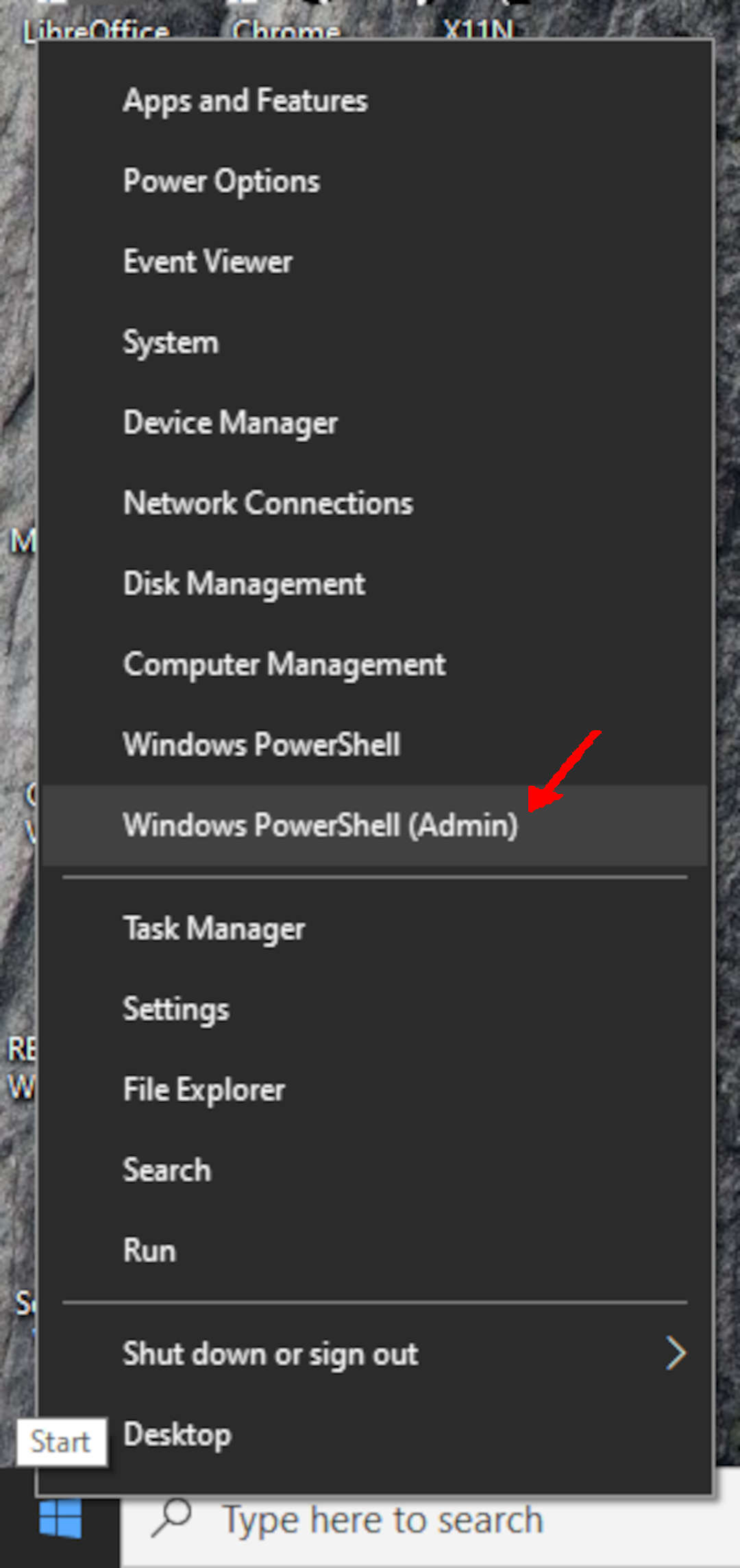
Run Windows PowerShell (Admin)
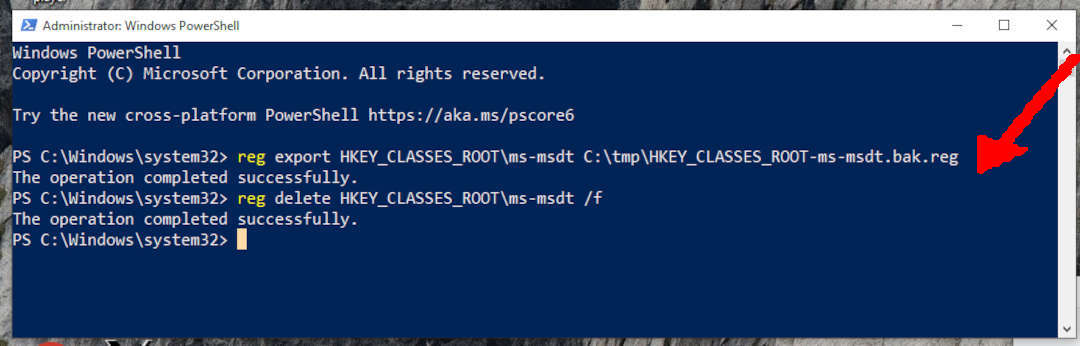
BACKUP THEN DELETE REGISTRY “MS-MSDT”
reg export HKEY_CLASSES_ROOT\ms-msdt C:\tmp\HKEY_CLASSES_ROOT-ms-msdt.bak.reg
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
DISCLAIMER
This is the WAY! This MEMO is mainly written for OWN PURPOSES. It is based on "Google Here, Google There, and Everywhere (GSGS)." Whether this is PLAGIARY or RESEARCH, there has never been a claim that this is an original work, nor is it necessarily the best solution, and not for Scopus consumption :). Please provide feedback, especially if you have alternative explanations. Hopefully, this note will be helpful in the future when you have forgotten how to solve this trivia problem.
© 2022-2022 --- C. BinKadal ---
About ---
Revision: 0020--26-Jul-2022.